User-Driven Approach to Preventing Unsanctioned Profile Modifications and Deletions in Cloud-Based Multi-Tenant Infrastructures
Keywords:
Authentication, cybersecurity, account hijacking, social engineering, Authentication TechniqueAbstract
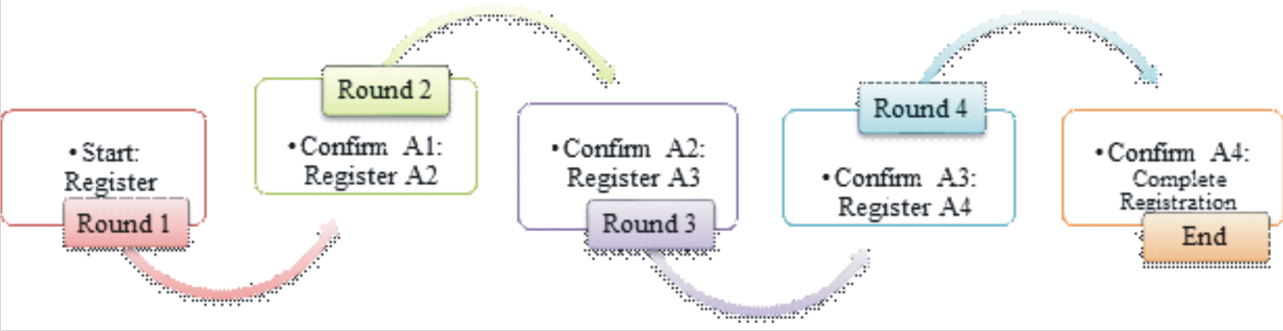
This study introduces a novel user-driven approach to counter unauthorized profile alteration and deletion in multi-tenant cloud environments. The researchers contend that conventional access control mechanisms are inadequate in mitigating insider threats and account hijackings, which can result from legitimate or unauthorized access to a cloud platform, with subsequent intentional or accidental modifications or deletions of data. To mitigate these threats, the researchers advocate for a user-driven approach that equips users with the ability to regulate access to their profiles utilizing the Serpentine Multifactor Authentication Technique (SeMFAT). The approach has two major components: the registration by validation process for registering authentication vectors and the authentication by validation procedure for authenticating the authentication vectors. The latter is activated when a user-secured action is triggered, based on a profile audit trail. The trail tracks all actions taken on a user's profile and activates the authentication by validation action to ensure that only users with verified privileges are granted the right to certain actions on their profiles. The authors assessed the efficacy of their approach by implementing a prototype on a multi-tenant cloud platform. 98% delivery success was recorded for SMS and emails response delivery, while a 100% success on preventing unauthorized profile alterations and deletions was recorded for all delivered messages. Overall, this study underscores the value of user-centric security measures in multi-tenant cloud settings, providing a feasible approach to thwarting both internal and external attacks since it is difficult to compromise all the user’s authentication vectors within a limited authentication session.